We can secure Logic app by controlling ips which can invoke logic app but we do not have this capability in Microsoft Flow. A Http trigger generates a unique link with SAS token in it, which is a public URL. Yes, this needs to be only shared with people who needs access to it but still it can be forwarded across and whoever gets access can trigger the flow.
Is there is any way we can secure it? I have recently implemented this in my http trigger based flow.
Each Http request has an referrer header associated with it. This is string passed by calling browser and provides some details of the caller. Example, If I am calling http trigger link from one of my sharepoint subsite and referral value looks like below..
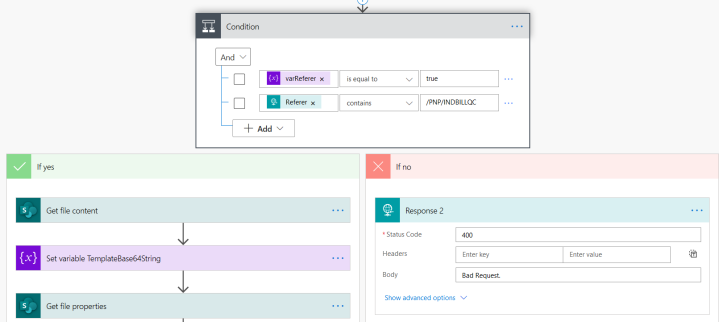
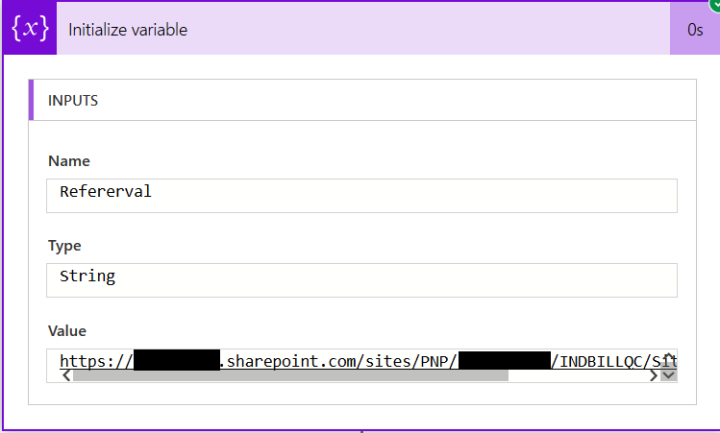 Now I can refer to this header value and look for Keywords OR path. E.g. Does my header includes ‘/PNP/INDBILLQC’. If not, return a response ‘Bad Request’. Proceed only if Yes. Something like below..
Now I can refer to this header value and look for Keywords OR path. E.g. Does my header includes ‘/PNP/INDBILLQC’. If not, return a response ‘Bad Request’. Proceed only if Yes. Something like below..
First check if Headers collection contains Referer….
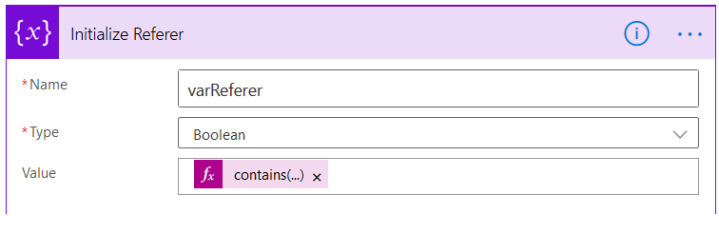
Each Http Request also has Useragent header. We can check that here…
contains(triggerOutputs()[‘Headers’],’User-Agent’)…
You can get the strings that these browsers generate and add a check. Example, following is what Chrome generated… You can actually add Chrome/64 string as a check if you want to be specific
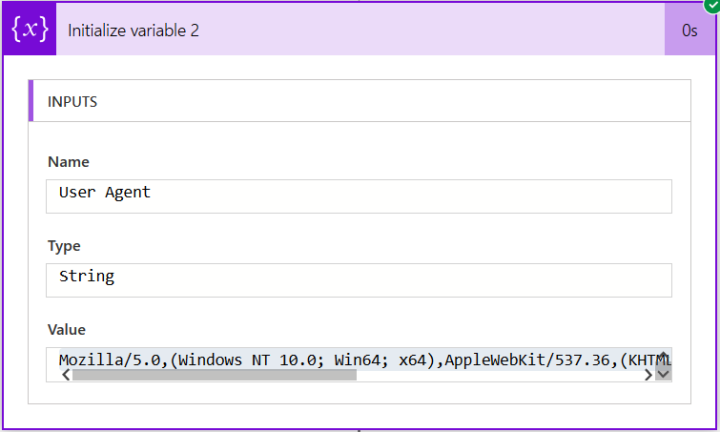
Mozilla/5.0,(Windows NT 10.0; Win64; x64),AppleWebKit/537.36,(KHTML, like Gecko),Chrome/64.0.3282.140,Safari/537.36,Edge/18.17763
